Cloud Security
First Look: Adallom's Behavior-Tracking Cloud Security

There’s no such thing as perfect data security, be it on premise or in the cloud. There will always be a risk of being compromised by both external and internal attacks.
What makes Menlo Park-based cloud security provider Adallom so intriguing is that its flagship product takes a markedly different approach to security on cloud-based enterprise apps, one that makes no discrepancies whether a potential attack is external or internal. The way it goes about doing that is novel, to say the least.
Adallom’s Elite History
Adallom’s digital security roots run deep. The company, founded in 2012, was the product of alumni from Unit 8200, the Israeli Defense Force’s elite signals intelligence unit. The company’s name is based on “Ad Halom,” a Hebrew saying that translates to “up to here,” referring to a last line of defense.
To wit, Adallom’s approach to security is to draw up a defensive line in a place far different from many comparable solutions. Instead of being installed locally on every device authorized for work use, Adallom bypasses that entirely, instead interfacing directly interfacing via API to all the cloud applications your company uses.
Rethinking SaaS Security
At the heart of Adallom is a feature it describes as the “heuristic persona.” What this translates to is tracking all the ways in which each individual in the organization interacts with the company’s SaaS apps.
By doing so Adallom is able to generate customized profiles of the normal user behavior for each team member, a process that takes around 60 days according to Tal Klein, Adallom’s vice president of marketing. After the 60 days administrators are invited to tweak settings to make sure things are aligned with existing company security policies.
With that combination of system-defined behavioral profiles and administrator-defined policies in hand Adallom monitors user actions on a real-time basis, scanning for discrepancies. When user activities pass a certain amount of standard deviations away from their average, a red flag goes up and the suspicious behavior is logged. Klein likened this mechanism to the way a bank protects credit cards.
This kind of automatic security response brings up the issue of potentially being locked out of your applications should you accidentally access a previously unused SaaS program without getting the proper security clearances. Klein, however, responded to this by pointing out that different security measures can be assigned to different levels of suspicious behavior. For example, simply opening up an app not related to one’s department might garner a minor flag, while more blatantly suspicious actions, like downloading all the files off a database directory or having the same user access apps from two different geographical locations in a short time frame are dealt with more strictly.
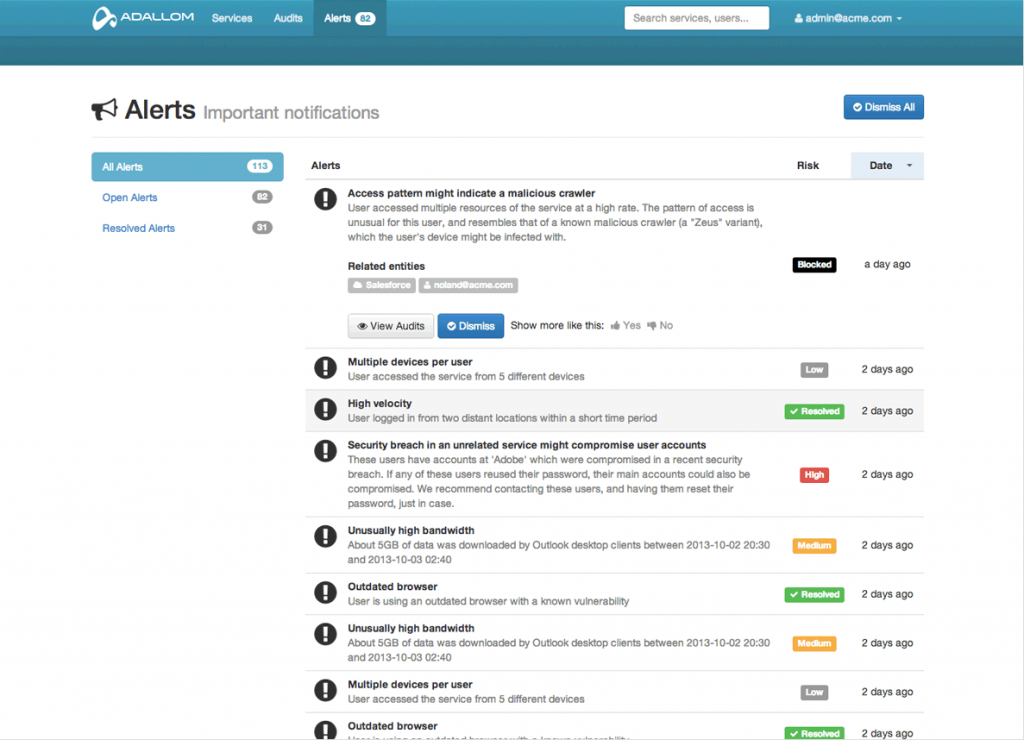
In spite of the complexity running under the hood, Adallom’s main dashboard interface is remarkably simple and clean. Though the heart of the application is in the way it seamlessly integrates into the authentication chain for all the different SaaS apps, the dashboard provides relatively informative views of top-level information. The administrator can generate logs of all flagged actions, track the actions of specific users and even get a real-time feed of all the actions happening across the organization’s apps, a feature that, while very cool to see in action, will no doubt get hectic to the point of making it only marginally useful for larger companies.
The Bottom Line
 One of the biggest challenges Adallom faces currently is convincing organizations of the viability of its approach. Klein said that it’s easy for managers to base their skepticism on a misinterpretation of how their SaaS applications work.
One of the biggest challenges Adallom faces currently is convincing organizations of the viability of its approach. Klein said that it’s easy for managers to base their skepticism on a misinterpretation of how their SaaS applications work.
While a SaaS app’s terms of service might guarantee security for all the company data stored on its offsite databases, that doesn’t necessarily make the SaaS provider liable for breaches that happen as a result of someone using an authorized power user account they obtained through social engineering, precisely the kind of behavior Adallom’s heuristic persona model reacts against.
Klein believes that Adallom and other products like it are part of what he describes as a “SaaS renaissance.”
“We had the SaaS revolution in the 2000s, but the SaaS renaissance will see even greater movements of enterprise onto the cloud,” he said, adding that the fundamental perks–cheaper TCOs, faster deployment and even better security–will eventually drive most if not all enterprise processes across the board into the cloud.
If that turns out to be the case then Adallom has a bright future and a lot of prospective clients coming down the pipe.
If you’re looking for next steps to find out more on enterprise security make sure to check out our comprehensive IT management resource page as well as our Top 10 Mobile Device Management Software report.