Endpoint Security
Why BYOD Is Like Cancer (And How Endpoint Security Is the Cure)

Despite its rapid adoption, BYOD is still a major security issue. Each phone, laptop and tablet connected to your network acts like a cancerous cell, growing your security risk and making your business susceptible to viruses and hacks. When your business is unable to control devices outside of the workplace, employees can leave company information exposed or use non-approved applications that pose a threat to the business.
Organizations have addressed this issue with mobile device management (MDM). But what happens when you allow a multitude of remote devices to access your company network? The security concerns don’t altogether disappear. MDM simply isn’t robust enough to handle it.
Endpoint Security: Why MDM Isn’t Enough
Endpoints are the dozens of phones, tablets and laptops remotely connected to your network. These endpoints wander freely outside of the workplace, soaking up hours of dangerous use during off-hours. While MDM is an efficient catch-all tool to manage and control BYOD devices for the workplace, the solution does not have the robust security features that would protect an enterprise from virus threats and compliance issues.
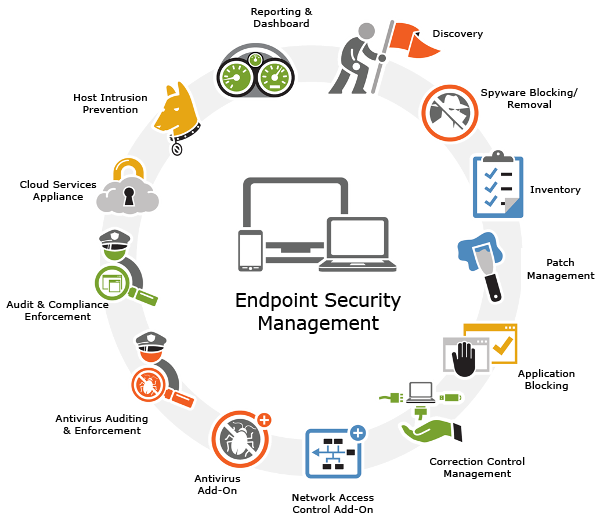
Acting much like an antivirus solution, endpoint security software protects the network against security threats caused by entry points (like a laptop or tablet) and ensures that your network is impenetrable. Endpoint security management software is housed in a centrally managed server within the network. From there, the server authenticates logins and updates device software, ensuring that each device meets all conditions before providing network access. Like its antivirus-software cousin, endpoint security management software protects the networks and endpoints against viruses and threats.
Most endpoint security solutions include a central dashboard with real-time reporting, antivirus auditing, endpoint tracking, application blocking and compliance enforcement. Endpoint security’s main differentiator from antivirus software is its ability to ensure endpoints are completely safe (with all necessary updates installed).
5 Top Endpoint Security Management Solutions
To get a quick peek into the industry, we’ve selected five leading endpoint security providers that should provide an insightful glimpse into the software’s capabilities.
1. Kaseya
Kaseya promises complete protection against viruses, worms and trojans. With its real-time protection, Kaseya discovers a virus while it is being accessed and terminates the operation to prevent the virus from activation. The solution integrates with its entire IT security suite, protecting not only endpoints but the entire system network. The solution includes security statuses, scheduled scans and threat logs to ensure your entire business is secure.
2. BeyondTrust PowerBroker
 PowerBroker is a multi-layered solution that is lightweight by nature. The solution is able to catalog complete system information, discover privilege data, provide endpoint configuration visibility, manage risk priority and identify machines that frequently move in and out of the network. In addition, PowerBroker can spot security weaknesses and provide custom assessments. PowerBroker is thorough, managing endpoints through its entire protection lifecycle, from its self-defined steps of discovery, assessment, comply and optimize.
PowerBroker is a multi-layered solution that is lightweight by nature. The solution is able to catalog complete system information, discover privilege data, provide endpoint configuration visibility, manage risk priority and identify machines that frequently move in and out of the network. In addition, PowerBroker can spot security weaknesses and provide custom assessments. PowerBroker is thorough, managing endpoints through its entire protection lifecycle, from its self-defined steps of discovery, assessment, comply and optimize.
3. IBM
I BM’s endpoint security provides protection and compliance with real-time visibility. IBM allows you to watch your solution fight against security threats in-the-moment with enforced configuration, patch compliance and the standard anti-malware tools. As you may expect with IBM, the solution can manage endpoints on a massive scale. This endpoint security software can control 70 operating systems in both physical and virtual endpoints, whether they are on or off the network.
BM’s endpoint security provides protection and compliance with real-time visibility. IBM allows you to watch your solution fight against security threats in-the-moment with enforced configuration, patch compliance and the standard anti-malware tools. As you may expect with IBM, the solution can manage endpoints on a massive scale. This endpoint security software can control 70 operating systems in both physical and virtual endpoints, whether they are on or off the network.
4. Symantec
 To Symantec, endpoint security is a step beyond its popular antivirus software. This solution brings security to both physical and virtual systems. Symantec identifies critical events instantly and works seamlessly between Mac and Windows operating systems. Symantec also includes multiple layering, including SONAR and Symantec Insight, as well as integration with VMware vShield for a more powerful performance.
To Symantec, endpoint security is a step beyond its popular antivirus software. This solution brings security to both physical and virtual systems. Symantec identifies critical events instantly and works seamlessly between Mac and Windows operating systems. Symantec also includes multiple layering, including SONAR and Symantec Insight, as well as integration with VMware vShield for a more powerful performance.
5. Lumension
 Lumension lets only authorized endpoints pass. Integrating with both application control and antivirus software, you can centrally manage and control applications. Lumension uses a whitelisting approach — a cloud based “trust score” used to automate whitelist maintenance. The solution also includes management tools, allowing you to see who is using what applications on which endpoints for total protection from BYOD issues.
Lumension lets only authorized endpoints pass. Integrating with both application control and antivirus software, you can centrally manage and control applications. Lumension uses a whitelisting approach — a cloud based “trust score” used to automate whitelist maintenance. The solution also includes management tools, allowing you to see who is using what applications on which endpoints for total protection from BYOD issues.
Cure Your Security Risk With These Next Steps
Want more information on endpoint security management? We at Business-Software.com have tirelessly researched and compiled the industry’s leaders in endpoint management software. You can read our findings by registering with us. Download the Top 10 Endpoint Security Management report to compare features, pricing, key customers and more. We wish you the best on your journey to find complete security in your business.