Endpoint Security
Bromium Secures Your Network with Hardware Virtualization

All networks can be compromised. As the cloud and mobile gain popularity, companies are struggling to keep access and data secure. But Bromium, hot off a $26.5M funding round, has the answer: hardware virtualization. We sat down with Bromium Director of Products Tal Klein to find out more about this novel approach.
To find out more about Bromium, visit their site or take a look at their product profile.
How was Bromium founded?
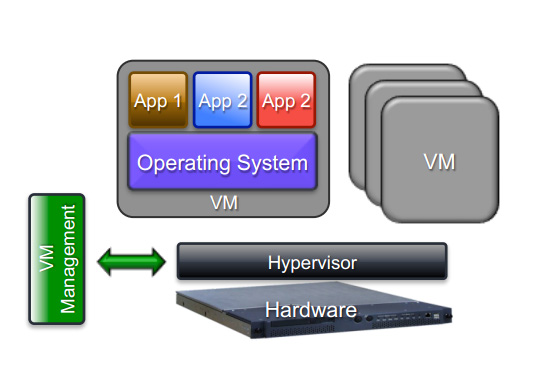
Bromium was founded as a provider of security software that focuses on protecting each end-user and their devices as opposed to firewalling the entire network. Our founders [Gaurav Banga and Simon Crosby] were inspired to take a radically different approach through the use of virtualization of tasks. Hardware virtualization is really the “secret sauce” of Bromium’s security solution.
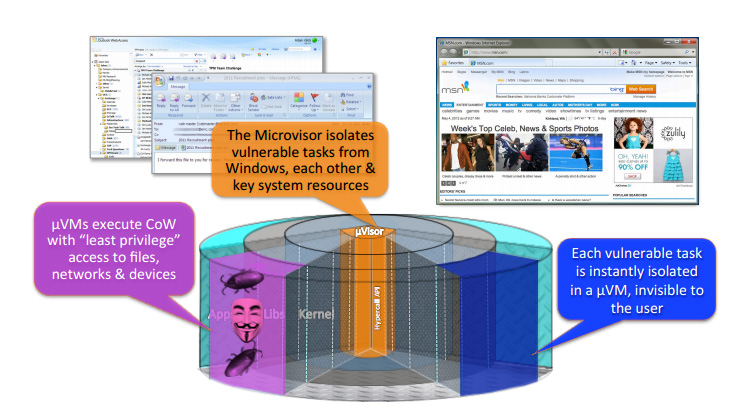
Our virtualization technology, Microvisor, places every application task on a single system inside its own micro-VM. These VMs are completely isolated from the device’s OS and can lock down harmful processes that try to deploy inside them.
In one or two sentence what would you say your company mission is?
Our mission as a company is to build systems that are, as we say, “trustworthy by design.” What I mean by that is that we want to give the users a system where any user on the network can bring in a new personal device like a laptop or a tablet without IT having to worry about what each end-user on the office network is doing on each of those devices.
What sets you apart from your competitors in the security segment? Why should, say, a mid-size business or small enterprise go with Bromium instead of just loading up Microsoft Security Essentials or Norton 360?
In many ways we’re actually complimenting solutions like the ones you mentioned in the interest of fighting malware. Look at it this way: imagine if you didn’t have to worry about any harmful data like malware or worms getting into your network from the web—how would that affect your approach to IT management, or the whole organization? Bromium aims to create that kind of environment.
Our perspective as a security provider is that end-users are humans. They make mistakes and click things they shouldn’t or access untrusted sites even when it’s against official policy. We build software around the idea that at the end of the day you can’t have full control over end-user behavior. By using self-contained micro-virtualized machines that automatically identify and isolate these harmful processes we can lock down a piece of malware as it deploys.
Are you guys still in beta stage with the product? If so what sort of challenges have you been facing in the testing you’ve done so far?
We’re still in beta stage right now, and there are several reasons for that. Actually, there are really two things still keeping us in beta. The first is that we’re committed to the idea of not going into GA (general availability) until the product is absolutely awesome. Second is that we’ve faced some challenges getting our beta testers comfortable working in a completely different, less restrictive security environment from what they’re used to.
One of the biggest challenges in talking with some of the companies we’re working with to beta Bromium is getting over a sort of philosophical divide of “First Protect, Then Detect” vs. “First Detect, Then Protect” in how to provide network security. Honestly, I don’t know of any user who’s actually clicked one of those security pop-ups they get from a piece of traditional security software on their workstation.
As an expert in the field, where do you think the security segment is right now, and where is it headed in the next 5 years? How will Bromium fit into that landscape?
My personal perspective on the security segment as it stands right now is that a lot of it is like the TSA at the airports—it’s essentially security theatre. Airport security can only find the guys carrying bombs in their luggage. They’re probably not going to find the kinds of unknown threats we’ve never seen deployed before except by luck. Traditional security solutions can only protect against know threats too, the ones already discovered, cracked and filed into a malware definitions database.
The future is adaptable solutions that identify threats on their own instead of referring to a centralized database of definitions. Bromium’s architecture is specifically for that kind of model. All processes can eventually be compromised, and we design our technology around that fact.
What sorts of challenges do you see coming up in this segment? How does Bromium plan to address them?
Malware is going to get more complex. We’ve already seen examples of this evolution with Stuxnet. Every process be compromised, so making individual processes as short-lived as possible must be the focus going forward. Bromium is built on comparatively little source code compared to competitors, just around 100,000 lines. Ultimately what you get with Bromium is a very tiny attack surface for malware. So even if they can be breached in the end, the goal here is to make security processes that are so costly to compromise that no one will bother to try.
What’s the most exciting thing about Bromium? Which particular features of technologies you excited about it?
I’m most excited about the commitment of our founders. They’re very accomplished people in this field and have veteran experience in working with virtual machines—the essence of the Bromium approach. It’s also exciting to be going forward with development knowing that second generation hardware virtualization like Microvisor is going to become the industry standard for security solutions going forward.
Looking for more information on Bromium or other enterprise security solutions? Compare leading endpoint security software platforms side by side in our free report on the Top 10 Endpoint Security Solutions.